|
 |
■ Bioresources information is available at the following URLs
|
 |
 |
■ Announcements
| The ex-post evaluation report of the NBRP has been released. |
| |
The results of the project selection for the “Genome information consolidation program”
(April 2011 to March 2012) of NBRP in the fiscal year 2011 have been announced!
|
[NBRP symposium] at the 83rd Annual Meeting of Genetics Society of Japan
September 20 and 22 (in the afternoons) |
|
 |
|
Research and Bioresources <No.11> Latest Information on Morning Glory Resources
Atsushi Hoshino (Model Animal Research Facility, National Institute for Basic Biology)
Eiji Nitasaka (Department of Biological Science, Graduate School of Sciences, Kyushu University)
Morning glory bioresources are unique to Japan, and many mutant strains isolated in the late Edo period are preserved by our institutions. In this article, we describe the present situation regarding morning glory bioresources, focusing on the advancements of the 2nd stage of the National BioResource Project (NBRP) in the last 4 years (fiscal years 2007−2010).
 Management of the 2 nd stage of the NBRP Morning Glory project |
The 1st stage of NBRP Morning Glory was initiated by Kyushu University, the core institution, and 2 sub-institutions, and the 2nd stage was administered by Kyushu University and the National Institute for Basic Biology (NIBB; a sub-institution). Kyushu University maintains strains of morning glory and related species, and NIBB maintains the DNA clones of these species. These institutions thus mutually complement each other and consolidate backup systems. |
 Strains of morning glory and related species |
We had collected 552 morning glory strains by the end of the last fiscal year in the 2nd stage of the project, and now hold 1750 stains in total, including the strains collected in the 1st stage. Domestic researchers and amateur collectors have been the primary depositors, but wild strains and related species have also been collected by overseas researchers. We cultivate about 2,500 plants of morning glory, comprising 500−800 strains, every year in order to renew strains, investigate and record their properties, and acquire seeds for distribution. Moreover, in order to examine the genotypes of strains that retain sterile mutations, we also cultivate up to tens of thousands of plants in greenhouses in winter, when the plants blossom early under short-day conditions. Using these cultivation processes, novel mutants have been discovered (Fig. 1). Intrinsic transposons with high transfer activities are thought to cause these mutations. |
 |
Fig. 1: Mutant morning glory strains identified in the 2nd stage of NBRP Morning Glory
| A: |
Defective right and left lobes and limited elongation of petals. |
| B: |
Tissues on the adaxial side replaced by abaxial tissues. |
| C: |
Atrophied leaves and flowers showing significantly mutated phenotypes. |
| D: |
No development of floral buds. |
| E: |
Novel maple-leaf mutant identified in commercial strains. |
| F: |
Night-blooming strains obtained from a natural group from Mexico by Prof. Emeritus Yoshiaki Yoneda, Shizuoka University. |
|
Morning glory is a short-day plant with extremely useful properties for research into floral transition, which can be induced by providing a dark period once during germination. However, brief light irradiation during the dark period will cancel the induction (a "light break"). Murasaki (Violet), a standard strain, has been widely used domestically and internationally as a resource for researching floral transition, and has appeared in more than 500 research journal articles. One of the reasons for the frequent use of Violet is that homogeneous seeds could previously be easily purchased from Marutane (a nursery company in Kyoto). However, the sale of Violet was discontinued when Prof. Masateru Shinozaki retired from Kyoto University, since he had been providing the seeds, produced through self-fertilization, to Marutane. In response to a strong request from researchers who had been using Violet, we decided to increase the production of the seeds as part of the NBRP Morning Glory project; however, the need to meet requests for several kilograms of seeds and to acquire homogeneous seeds was expected to present a significant challenge. Thus, the core institution constructed a new isolation chamber (Fig. 2) to increase the production of homogeneous seeds that are free from impurities, and has also initiated commissioned production by a nursery company on a trial basis since the start of this fiscal year. |
 |
Fig. 2: Cultivation of Violet, a standard strain, inside the screened isolation chamber, which prevents hybridization mediated by insects. |
|
 BAC clones of morning glory |
In the 1st stage of the NBRP, EST clones were primarily collected; however, in the 2nd stage, 55,296 BAC clones were collected and distributed. BAC clones were constructed from DNA extracted from the Tokyo Kokei Standard (Q1065) strain immediately after its germination, and we prepared 2 libraries using different sets of restriction enzymes for genome fragmentation. The average length of the clones is around 100 kb and the genome coverage is 5−6×. The morning glory genome has not been sequenced and neither have the BAC clone sequences; thus, we developed a 4-dimensional DNA pool ∗1 (Fig. 3) as a system for distributing the clones. We initially provide the total DNA pool and ask users to conduct screening, and then continue to provide the clones that show positive results. The size of the morning glory genome is estimated to be 800−1000 Mbp, and genome sequencing is currently being conducted with support of a Grant-in-Aid for Scientific Research on Innovative Areas − Genome Support Project, provided by the Ministry of Education, Culture, Sports, Science and Technology. Terminal sequences of the BAC clones, which were collected as a part of the project, will also be prepared for distribution. In addition, a DNA pool was developed in collaboration with Prof. Naruse and Dr. Takehana at NBRP Medaka (NIBB). I would like to take this opportunity to acknowledge their cooperation. |
 |
Fig. 3: The 4-dimensional BAC DNA pool.
BAC clones contained in seventy-two 384-well plates were mixed in 4 different patterns, and the extracted DNAs were preserved in six 96-well plates and 12 tubes. |
|
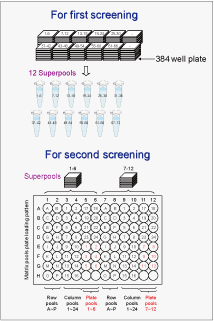 |
∗1 Screening using a clone pool
A method for screening target clones with a small number of experiments. If seventy-two 384-well plates (16 × 24 wells each) containing BAC clones of morning glory are available, the following 4 types of DNA pools (4 dimensions) are prepared, with 6 plates per set:
|
| 1) |
Pools containing all 2,304 clones from 6 plates (384 wells × 6 plates): 12 sets |
| 2) |
Pools of the 144 clones in each row of each plate (24 wells/row × 6 plates): 16 pools × 12 sets |
| 3) |
Pools of the 96 clones in each column of each plate (16 wells/column × 6 plates): 24 pools × 12 sets |
| 4) |
Pools of the 384 clones on each plate: 6 pools × 12 sets |
First, 12 polymerase chain reactions (PCRs) are conducted using each type 1) pool as a template. Next, 46 reactions (16 + 24 + 6) are conducted using the pools 2) − 4) that contain the target clones, based on the first set of reactions. Target clones can thus be selected by 58 PCRs in total. The type 1) pools of BAC clones are contained in 12 tubes, and pools 2) − 4) are in six 96-well plates. |
|
|
 Publicity and educational activities |
The NBRP Morning Glory group hosts workshops for the morning glory research community. The 5th and 6th Morning Glory Workshops were held in 2008 and 2010, respectively, at NIBB. The next workshop will take place next summer at Kyushu University.
Next month (September 6−8, 2011), at Kyushu University, a morning glory observation tour will also be organized as part of the 29th Annual Meeting of the Japanese Society of Plant Cell and Molecular Biology.
In future, we aim to develop resources that are more useful for researchers, by integrating information on the strains and DNA clones with genome sequences. We sincerely appreciate the continued support of all the morning glory researchers and community members. |
|
|
Virus Threats to Smart Phones |
Malwares targeting explosively popular Android phones

Three cell phone giants in Japan, NTT Docomo, KDDI, and SoftBank Mobile, introduced many new models of Android smart phones (Fig. 1) into the market during the 2011 summer selling season, and are strongly pushing sales of the models by emphasizing their greater convenience. Consequently, the number of Android phone users has dramatically increased and exceeded that of iPhone users, making this the most popular type of cell phone both in Japan and worldwide.
In proportion to the increasing number of users, malwares (malicious programs containing viruses) targeting Android phones have also become increasingly widespread this year, and malicious applications and financially motivated malwares have been found in the Android market (Fig. 2), which has previously been considered safe.
|

| |
Fig. 1: Smart phones |
| • |
Cell phones with expandable functions via installation of applications of the users' choice |
| • |
Internet connection is based on use |
|
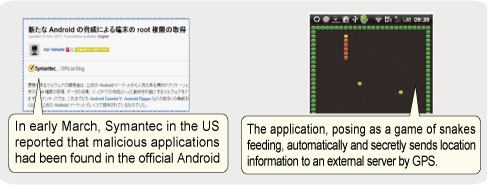
Fig. 2: Examples of malwares in Android phones |

| |
Open-source and therefore high-risk Android phones
Android OS, developed by Google, is characterized by its openness: It is license-free, its specifications are released, and applications can be freely distributed. However, this openness makes malwares easy to develop, and therefore security measures equal to or higher than those used in PCs are indispensable. In addition, since more personal information is often stored in cell phones than on PCs, malwares targeting Android phones are predicted to increase explosively in number in the future.
Security measures for Android phones
Google does not provide all the tools and information necessary for security, and therefore users need to select and combine the products and services provided by third parties. As long as Android phones are being used for communicating information on the Internet, software for security measures is essential. In addition, users have to take precautions not to install dubious applications.
Select security software based on functions available
A wide range of paid and free security software is provided by many companies; however, software containing the following functions is recommended:
- Virus scanning of main memory and SD memory cards
- Blocking of downloads of malicious applications
- Blocking of unwanted phone calls and text messages such as SMS∗1
- Remote data elimination or lock function if phone is lost
∗1 Abbreviation for "short message service," in which a transmitter pays the transmission cost of a message and a receiver receives the message free of charge.
Ensure that you download applications from reliable sites and check permissions at installation
|
|
| |
At the installation of an Android application, a confirmation screen always appears, showing information accessed by the application such as personal information, GPS location information, and network access (Fig. 3). Upon installation, ensure that you make the small effort to check whether there is any questionable content in the application and information that will be accessed.
Nevertheless, since it is difficult to find out whether an application to be installed is potentially malicious, using reliable applications such as those provided by cell phone companies is recommended. |
|
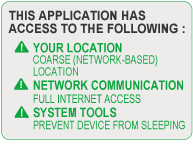
Fig. 3: Make sure to check confirmation screen regarding access information |
|
--------------------------------------
Security measures are summarized in the following diagram. Let's make full use of a smart phone with constant consideration of the important data stored in it!
|
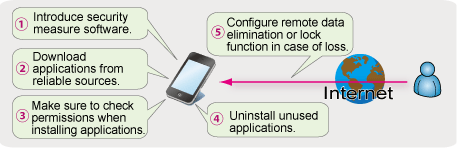
Figure: Summary of countermeasures |
(Takehiro Yamakawa)
|
|